Welcome to Breakthrough Genomics
Breakthrough Genomics is a technology-driven company at the forefront of AI-powered genomic data analysis and clinical interpretation. It also provides genetic testing for NICU/PICU care, rare diseases, and early cancer screening through its CAP/CLIA-certified laboratory.
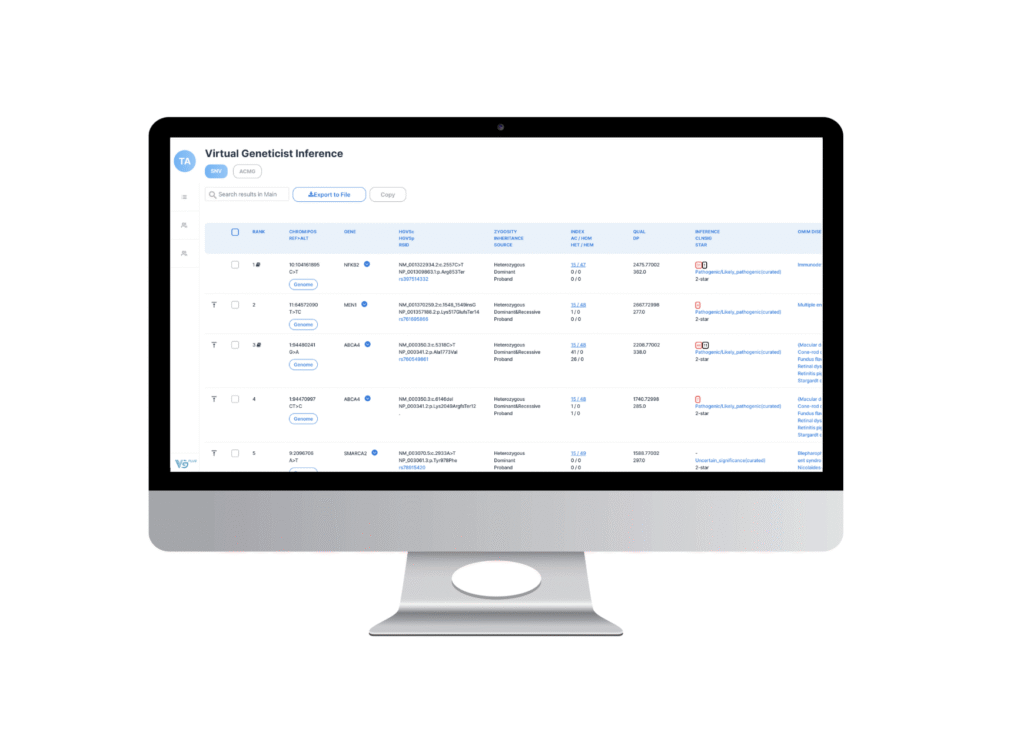
At the heart of our innovation is Virtual Geneticist®, a first-of-its-kind clinical interpretation platform powered by AI. This platform streamlines genomic data interpretation, enabling users to rapidly and accurately identify disease-causing variants. By accelerating and enhancing the diagnostic process, Virtual Geneticist is redefining the future of rare disease diagnostics—making it faster, smarter, and more accessible.
Introducing Virtual Geneticist® (VG)
Virtual Geneticist® is Breakthrough Genomics’ proprietary AI-powered clinical interpretation platform, developed to accelerate and enhance the analysis of whole exome (WES) and whole genome (WGS) sequencing data. Purpose-built for rare disease diagnostics, VG harnesses advanced AI models to rapidly and accurately prioritize potential disease-causing variants, drawing on a comprehensive knowledge base of over 180 million variants with automated ACMG classifications and 11 million interpreted variant–literature associations.
The platform delivers ACMG-guided interpretations through structured, evidence-based summaries and has demonstrated improved diagnostic outcomes in previously unsolved clinical cases. Designed for speed, scalability, and ease of integration, Virtual Geneticist® fits seamlessly into standard laboratory workflows and supports all major sequencing technologies.
Press Releases
WINNER
CIF 2024
INNOVATION
AWARD



Testimonials
Why Choose Us
-
AI-Driven Variant Prioritization
-
Accessible and Cost-Efficient
-
Fast, Scalable Turnaround
-
Sequencer-Agnostic and Workflow-Compatible
-
Transparent, Evidence-Backed Interpretations
-
Laboratory-Validated Integration
Our Services

Clinical Genomic Analysis with Next-Generation Computing
Breakthrough Genomics leverages the company’s proprietary technology and hands-on experience in clinical genomics to help solve the biggest challenges
in precision medicine.
LEARN MORE
Early Cancer Detections
The company’s early cancer detection tests revolutionize screening for a range of cancers, including pancreatic cancer, colon cancer, stomach cancer, liver cancer, and more, using just a simple tube of blood. These tests have received prestigious recognition, including the FDA Breakthrough Device grant and the EU IVDD certificate.
LEARN MORE
Advanced Genetic Tests
Breakthrough Genomics offers a wide range of advanced genetic tests from hereditary cancer and cardiovascular screening to rare disease diagnosis and rapid Whole Genome and Whole Exome tests for the NICU and PICU.
LEARN MORE